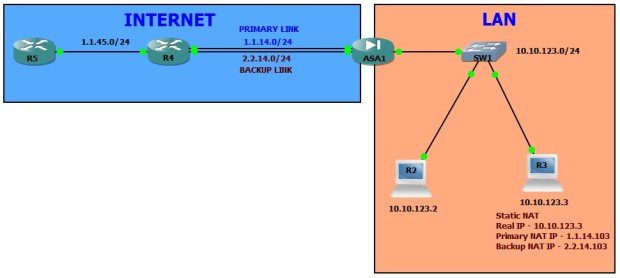
Objective of this task:
- Configure floating static route with object tracking
- Configure Dynamic NAT via Primary and Backup Link
- Configure Static NAT with auto failover between Primary and Backup Link
Basic Configuration on ASA: interface GigabitEthernet0 nameif outside security-level 0 ip address 1.1.14.1 255.255.255.0 ! interface GigabitEthernet1 nameif outside-2 security-level 0 ip address 2.2.14.1 255.255.255.0 ! interface GigabitEthernet2 nameif inside security-level 100 ip address 10.10.123.1 255.255.255.0 !
- Primary internet link IP subnet is 1.1.14.0/24 and ISP GW IP is 1.1.14.4.
- Backup internet link IP subnet is 2.2.14.0/24 and ISP GW IP is 2.2.14.4
- We will track reachability to IP address 4.4.4.4 via primary internet link to confirm if it is working fine.
# Configure static route to reach IP address 4.4.4.4 via primary internet link route outside 4.4.4.4 255.255.255.255 1.1.14.4 # Create SLA Monitor session sla monitor 101 type echo protocol ipIcmpEcho 4.4.4.4 interface outside num-packets 5 frequency 10 sla monitor schedule 101 life forever start-time now # Create track session track 1 rtr 101 reachability # Configure default route via primary internet link with tracking route outside 0.0.0.0 0.0.0.0 1.1.14.4 1 track 1 # Configure default route via backup internet link with higher administrative distance (i.e, 200, default AD is 1 for static route) route outside-2 0.0.0.0 0.0.0.0 2.2.14.4 200 # Configure Dynamic NAT rule for LAN users to access internet via primary or backup internet link object network ANY subnet 0.0.0.0 0.0.0.0 ! object network ANY-2 subnet 0.0.0.0 0.0.0.0 ! object network ANY nat (inside,outside) dynamic interface ! object network ANY-2 nat (inside,outside-2) dynamic interface
Verify default route and internet access
# Verify SLA Monitor configuration ASA# show sla monitor configuration SA Agent, Infrastructure Engine-II Entry number: 101 Owner: Tag: Type of operation to perform: echo Target address: 4.4.4.4 Interface: outside Number of packets: 5 Request size (ARR data portion): 28 Operation timeout (milliseconds): 5000 Type Of Service parameters: 0x0 Verify data: No Operation frequency (seconds): 10 Next Scheduled Start Time: Start Time already passed Group Scheduled : FALSE Life (seconds): Forever Entry Ageout (seconds): never Recurring (Starting Everyday): FALSE Status of entry (SNMP RowStatus): Active Enhanced History: # Verify SLA Monitor operational status ASA# show sla monitor operational-state Entry number: 101 Modification time: 09:54:01.469 UTC Sat Aug 1 2015 Number of Octets Used by this Entry: 1480 Number of operations attempted: 34 Number of operations skipped: 0 Current seconds left in Life: Forever Operational state of entry: Active Last time this entry was reset: Never Connection loss occurred: FALSE Timeout occurred: FALSE Over thresholds occurred: FALSE Latest RTT (milliseconds): 8 Latest operation start time: 09:59:31.479 UTC Sat Aug 1 2015 Latest operation return code: OK RTT Values: RTTAvg: 8 RTTMin: 1 RTTMax: 20 NumOfRTT: 5 RTTSum: 42 RTTSum2: 602 # Verify track status ASA# show track Track 1 Response Time Reporter 101 reachability Reachability is Up 2 changes, last change 00:05:45 Latest operation return code: OK Latest RTT (millisecs) 4 Tracked by: STATIC-IP-ROUTING 0 # Verify routing ASA# show run route route outside 0.0.0.0 0.0.0.0 1.1.14.4 1 track 1 route outside-2 0.0.0.0 0.0.0.0 2.2.14.4 200 route outside 4.4.4.4 255.255.255.255 1.1.14.4 1 ASA# sh route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 1.1.14.4 to network 0.0.0.0 C 1.1.14.0 255.255.255.0 is directly connected, outside C 2.2.14.0 255.255.255.0 is directly connected, outside-2 S 4.4.4.4 255.255.255.255 [1/0] via 1.1.14.4, outside C 10.10.123.0 255.255.255.0 is directly connected, inside S* 0.0.0.0 0.0.0.0 [1/0] via 1.1.14.4, outside # Ping internet IP address 5.5.5.5 (It is configured on R5) R2#ping 5.5.5.5 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 24/36/48 ms # Verify NAT on ASA ASA# show xlate 3 in use, 3 most used Flags: D - DNS, i - dynamic, r - portmap, s - static, I - identity, T - twice NAT from inside:10.10.123.3 to outside-2:2.2.14.103 flags s idle 0:09:24 timeout 0:00:00 NAT from inside:10.10.123.3 to outside:1.1.14.103 flags s idle 0:09:30 timeout 0:00:00 ICMP PAT from inside:10.10.123.2/2 to outside:1.1.14.1/35590 flags ri idle 0:00:28 timeout 0:00:30 ASA# show conn address 5.5.5.5 1 in use, 4 most used ICMP outside 5.5.5.5:0 inside 10.10.123.2:3, idle 0:00:00, bytes 72 # Let's simulate primary internet link failure # Shutdown int f0/0 on R4 R4#sh run int f0/0 Building configuration... Current configuration : 92 bytes ! interface FastEthernet0/0 ip address 1.1.14.4 255.255.255.0 speed 100 full-duplex end R4#conf t Enter configuration commands, one per line. End with CNTL/Z. R4(config)#int f0/0 R4(config-if)#shut R4(config-if)# *Mar 1 00:13:08.571: %LINK-5-CHANGED: Interface FastEthernet0/0, changed state to administratively down *Mar 1 00:13:09.571: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to down R4(config-if)# # Verify Track status on ASA ASA# show track Track 1 Response Time Reporter 101 reachability Reachability is Down 3 changes, last change 00:00:31 Latest operation return code: Timeout Tracked by: STATIC-IP-ROUTING 0 # Verify Routing ASA# show route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 2.2.14.4 to network 0.0.0.0 C 1.1.14.0 255.255.255.0 is directly connected, outside C 2.2.14.0 255.255.255.0 is directly connected, outside-2 S 4.4.4.4 255.255.255.255 [1/0] via 1.1.14.4, outside C 10.10.123.0 255.255.255.0 is directly connected, inside S* 0.0.0.0 0.0.0.0 [200/0] via 2.2.14.4, outside-2 # As you see in above output it has selected default route via backup ISP GW (2.2.14.4) now. # Verify Internet access from LAN and NAT status on ASA. Now LAN subnet is dynamically NAT'ed to backup interface. R2#ping 5.5.5.5 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 24/40/64 ms ASA# show xlate 3 in use, 5 most used Flags: D - DNS, i - dynamic, r - portmap, s - static, I - identity, T - twice NAT from inside:10.10.123.3 to outside-2:2.2.14.103 flags s idle 0:18:18 timeout 0:00:00 NAT from inside:10.10.123.3 to outside:1.1.14.103 flags s idle 0:18:24 timeout 0:00:00 ICMP PAT from inside:10.10.123.2/6 to outside-2:2.2.14.1/5805 flags ri idle 0:00:39 timeout 0:00:30 ASA# show conn address 5.5.5.5 1 in use, 6 most used ICMP outside-2 5.5.5.5:0 inside 10.10.123.2:6, idle 0:00:00, bytes 72 # Let's restore primary internet link R4(config-if)#no shut R4(config-if)#end R4# *Mar 1 00:22:12.595: %SYS-5-CONFIG_I: Configured from console by console R4# *Mar 1 00:22:13.935: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:22:14.935: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up # Track status is UP now ASA# show track Track 1 Response Time Reporter 101 reachability Reachability is Up 4 changes, last change 00:00:28 Latest operation return code: OK Latest RTT (millisecs) 8 Tracked by: STATIC-IP-ROUTING 0 # Verify Routing ASA# show route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 1.1.14.4 to network 0.0.0.0 C 1.1.14.0 255.255.255.0 is directly connected, outside C 2.2.14.0 255.255.255.0 is directly connected, outside-2 S 4.4.4.4 255.255.255.255 [1/0] via 1.1.14.4, outside C 10.10.123.0 255.255.255.0 is directly connected, inside S* 0.0.0.0 0.0.0.0 [1/0] via 1.1.14.4, outside
So everything is working as expected, default route is used via primary link when track object IP 4.4.4.4 is reachable and when there is any issue with the primary link, i.e., IP 4.4.4.4 is not reachable via primary link, then this default route is removed and backup link become active. Also NAT translations are done based on the outgoing interface used by default route.
Now we have another requirement, We have a server (10.10.123.3) in LAN which need to be accessed from internet. First, we should have static NAT to be created for this server.
We will create two static NAT entries for this server. So that it can be accessed via either IP and internet link (Primary/Backup)
# Define Objects object network SERVER-R3-PRIMARY host 10.10.123.3 ! object network SERVER-R3-BACKUP host 10.10.123.3 # Configure NAT Rules object network SERVER-R3-PRIMARY nat (inside,outside) static 1.1.14.103 ! object network SERVER-R3-BACKUP nat (inside,outside-2) static 2.2.14.103 # Verify reachability from Internet (R5) to Server (Real IP: 10.10.123.3, Primary NAT: 1.1.14.103) R5#ping 1.1.14.103 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.14.103, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 36/39/40 ms # Verify NAT status on ASA ASA# show xlate 2 in use, 5 most used Flags: D - DNS, i - dynamic, r - portmap, s - static, I - identity, T - twice NAT from inside:10.10.123.3 to outside-2:2.2.14.103 flags s idle 0:36:19 timeout 0:00:00 NAT from inside:10.10.123.3 to outside:1.1.14.103 flags s idle 0:00:11 timeout 0:00:00 ASA# show conn address 10.10.123.3 1 in use, 6 most used ICMP outside 1.1.45.5:5 inside 10.10.123.3:0, idle 0:00:00, bytes 72 # Primary internet link is down now and default route is changed via backup ISP GW now ASA# show track Track 1 Response Time Reporter 101 reachability Reachability is Down 5 changes, last change 00:00:01 Latest operation return code: Timeout Tracked by: STATIC-IP-ROUTING 0 ASA# show route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 2.2.14.4 to network 0.0.0.0 C 1.1.14.0 255.255.255.0 is directly connected, outside C 2.2.14.0 255.255.255.0 is directly connected, outside-2 S 4.4.4.4 255.255.255.255 [1/0] via 1.1.14.4, outside C 10.10.123.0 255.255.255.0 is directly connected, inside S* 0.0.0.0 0.0.0.0 [200/0] via 2.2.14.4, outside-2 # The Server is still reachable from internet via backup NAT IP R5#ping 2.2.14.103 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2.2.14.103, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 36/40/48 ms # Verify NAT and connection status on ASA ASA# sh xlate 2 in use, 5 most used Flags: D - DNS, i - dynamic, r - portmap, s - static, I - identity, T - twice NAT from inside:10.10.123.3 to outside-2:2.2.14.103 flags s idle 0:00:00 timeout 0:00:00 NAT from inside:10.10.123.3 to outside:1.1.14.103 flags s idle 0:04:03 timeout 0:00:00 ASA# show conn address 10.10.123.3 1 in use, 6 most used ICMP outside-2 1.1.45.5:10 inside 10.10.123.3:0, idle 0:00:00, bytes 72
Good Luck! 🙂