We will discuss route-leaking between VRFs using different import-map techniques in this session.
Here is the network topology for our discussion.
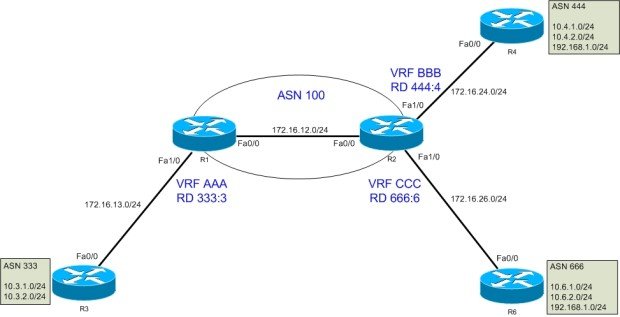
Task requirement: On R1, VRF AAA should import prefix 10.4.2.0/24 from ASN 444 and 10.6.1.0/24 from ASN 666.
Pre-Configuration of devices:
R1:
hostname R1
!
vrf definition AAA
rd 333:3
!
address-family ipv4
route-target export 333:3
route-target import 333:3
exit-address-family
!
interface Loopback0
ip address 172.16.0.1 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 172.16.12.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface FastEthernet1/0
vrf forwarding AAA
ip address 172.16.13.1 255.255.255.0
!
router ospf 1
log-adjacency-changes
!
router bgp 100
bgp router-id 172.16.0.1
no bgp default ipv4-unicast
no bgp default route-target filter
bgp log-neighbor-changes
neighbor 172.16.0.2 remote-as 100
neighbor 172.16.0.2 update-source Loopback0
!
address-family ipv4
no synchronization
no auto-summary
exit-address-family
!
address-family vpnv4
neighbor 172.16.0.2 activate
neighbor 172.16.0.2 send-community extended
exit-address-family
!
address-family ipv4 vrf AAA
no synchronization
redistribute connected
neighbor 172.16.13.3 remote-as 333
neighbor 172.16.13.3 activate
exit-address-family
!
end
R2:
hostname R2
!
vrf definition BBB
rd 444:4
!
address-family ipv4
route-target export 444:4
route-target import 444:4
exit-address-family
!
vrf definition CCC
rd 666:6
!
address-family ipv4
route-target export 666:6
route-target import 666:6
exit-address-family
!
interface Loopback0
ip address 172.16.0.2 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 172.16.12.2 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface FastEthernet1/0
vrf forwarding BBB
ip address 172.16.24.2 255.255.255.0
!
interface FastEthernet1/1
vrf forwarding CCC
ip address 172.16.26.2 255.255.255.0
!
router ospf 1
log-adjacency-changes
!
router bgp 100
bgp router-id 172.16.0.2
no bgp default ipv4-unicast
no bgp default route-target filter
bgp log-neighbor-changes
neighbor 172.16.0.1 remote-as 100
neighbor 172.16.0.1 update-source Loopback0
!
address-family ipv4
no synchronization
no auto-summary
exit-address-family
!
address-family vpnv4
neighbor 172.16.0.1 activate
neighbor 172.16.0.1 send-community extended
exit-address-family
!
address-family ipv4 vrf BBB
no synchronization
redistribute connected
neighbor 172.16.24.4 remote-as 444
neighbor 172.16.24.4 activate
exit-address-family
!
address-family ipv4 vrf CCC
no synchronization
redistribute connected
neighbor 172.16.26.6 remote-as 666
neighbor 172.16.26.6 activate
exit-address-family
!
R3:
hostname R3
!
interface Loopback1
ip address 10.3.1.1 255.255.255.0
!
interface Loopback2
ip address 10.3.2.1 255.255.255.0
!
interface FastEthernet0/0
ip address 172.16.13.3 255.255.255.0
!
router bgp 333
no synchronization
bgp router-id 172.16.13.3
bgp log-neighbor-changes
network 10.3.1.0 mask 255.255.255.0
network 10.3.2.0 mask 255.255.255.0
neighbor 172.16.13.1 remote-as 100
no auto-summary
!
R4:
hostname R4
!
interface Loopback1
ip address 10.4.1.1 255.255.255.0
!
interface Loopback2
ip address 10.4.2.1 255.255.255.0
!
interface Loopback192
ip address 192.168.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 172.16.24.4 255.255.255.0
!
router bgp 444
no synchronization
bgp router-id 172.16.24.4
bgp log-neighbor-changes
network 10.4.1.0 mask 255.255.255.0
network 10.4.2.0 mask 255.255.255.0
network 192.168.1.0
neighbor 172.16.24.2 remote-as 100
no auto-summary
!
R6:
hostname R6
!
interface Loopback1
ip address 10.6.1.1 255.255.255.0
!
interface Loopback2
ip address 10.6.2.1 255.255.255.0
!
interface Loopback192
ip address 192.168.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 172.16.26.6 255.255.255.0
!
router bgp 666
no synchronization
bgp router-id 172.16.26.6
bgp log-neighbor-changes
network 10.6.1.0 mask 255.255.255.0
network 10.6.2.0 mask 255.255.255.0
network 192.168.1.0
neighbor 172.16.26.2 remote-as 100
no auto-summary
!
All BGP neighborships are UP and Routers are advertising their respective prefixes into BGP.
R1#sh bgp all summary
For address family: VPNv4 Unicast
BGP router identifier 172.16.0.1, local AS number 100
BGP table version is 4, main routing table version 4
3 network entries using 456 bytes of memory
3 path entries using 156 bytes of memory
5/2 BGP path/bestpath attribute entries using 660 bytes of memory
1 BGP AS-PATH entries using 24 bytes of memory
3 BGP extended community entries using 72 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 1368 total bytes of memory
BGP activity 6/3 prefixes, 6/3 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
172.16.0.2 4 100 8 4 4 0 0 00:01:15 0
172.16.13.3 4 333 6 3 4 0 0 00:01:15 2
R1#sh bgp vpnv4 unicast all
BGP table version is 12, local router ID is 172.16.0.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 333:3 (default for vrf AAA)
*> 10.3.1.0/24 172.16.13.3 0 0 333 i
*> 10.3.2.0/24 172.16.13.3 0 0 333 i
*> 172.16.13.0/24 0.0.0.0 0 32768 ?
Route Distinguisher: 444:4
*>i10.4.1.0/24 172.16.0.2 0 100 0 444 i
*>i10.4.2.0/24 172.16.0.2 0 100 0 444 i
*>i172.16.24.0/24 172.16.0.2 0 100 0 ?
*>i192.168.1.0 172.16.0.2 0 100 0 444 i
Route Distinguisher: 666:6
*>i10.6.1.0/24 172.16.0.2 0 100 0 666 i
*>i10.6.2.0/24 172.16.0.2 0 100 0 666 i
*>i172.16.26.0/24 172.16.0.2 0 100 0 ?
*>i192.168.1.0 172.16.0.2 0 100 0 666 i
R2#sh bgp all summary
For address family: VPNv4 Unicast
BGP router identifier 172.16.0.2, local AS number 100
BGP table version is 9, main routing table version 9
8 network entries using 1216 bytes of memory
8 path entries using 416 bytes of memory
6/4 BGP path/bestpath attribute entries using 792 bytes of memory
2 BGP AS-PATH entries using 48 bytes of memory
2 BGP extended community entries using 48 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 2520 total bytes of memory
BGP activity 22/14 prefixes, 22/14 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
172.16.0.1 4 100 6 9 9 0 0 00:01:40 0
172.16.24.4 4 444 6 6 9 0 0 00:01:45 3
172.16.26.6 4 666 6 6 9 0 0 00:01:45 3
R2#sh bgp vpnv4 unicast all
BGP table version is 12, local router ID is 172.16.0.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 333:3
*>i10.3.1.0/24 172.16.0.1 0 100 0 333 i
*>i10.3.2.0/24 172.16.0.1 0 100 0 333 i
*>i172.16.13.0/24 172.16.0.1 0 100 0 ?
Route Distinguisher: 444:4 (default for vrf BBB)
*> 10.4.1.0/24 172.16.24.4 0 0 444 i
*> 10.4.2.0/24 172.16.24.4 0 0 444 i
*> 172.16.24.0/24 0.0.0.0 0 32768 ?
*> 192.168.1.0 172.16.24.4 0 0 444 i
Route Distinguisher: 666:6 (default for vrf CCC)
*> 10.6.1.0/24 172.16.26.6 0 0 666 i
*> 10.6.2.0/24 172.16.26.6 0 0 666 i
*> 172.16.26.0/24 0.0.0.0 0 32768 ?
*> 192.168.1.0 172.16.26.6 0 0 666 i
R3#sh ip bgp summary
BGP router identifier 172.16.13.3, local AS number 333
BGP table version is 29, main routing table version 29
3 network entries using 384 bytes of memory
3 path entries using 156 bytes of memory
2/2 BGP path/bestpath attribute entries using 248 bytes of memory
1 BGP AS-PATH entries using 24 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 812 total bytes of memory
BGP activity 14/11 prefixes, 15/12 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
172.16.13.1 4 100 11 12 29 0 0 00:07:10 1
R3#sh ip bgp
BGP table version is 29, local router ID is 172.16.13.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.3.1.0/24 0.0.0.0 0 32768 i
*> 10.3.2.0/24 0.0.0.0 0 32768 i
r> 172.16.13.0/24 172.16.13.1 0 0 100 ?
R3#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.3.1.0/24 is directly connected, Loopback1
L 10.3.1.1/32 is directly connected, Loopback1
C 10.3.2.0/24 is directly connected, Loopback2
L 10.3.2.1/32 is directly connected, Loopback2
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.13.0/24 is directly connected, FastEthernet0/0
L 172.16.13.3/32 is directly connected, FastEthernet0/0
R4#sh ip bgp sum
BGP router identifier 172.16.24.4, local AS number 444
BGP table version is 31, main routing table version 31
4 network entries using 512 bytes of memory
4 path entries using 208 bytes of memory
2/2 BGP path/bestpath attribute entries using 248 bytes of memory
1 BGP AS-PATH entries using 24 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 992 total bytes of memory
BGP activity 14/10 prefixes, 17/13 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
172.16.24.2 4 100 13 14 31 0 0 00:08:25 1
R4#sh ip bgp
BGP table version is 31, local router ID is 172.16.24.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.4.1.0/24 0.0.0.0 0 32768 i
*> 10.4.2.0/24 0.0.0.0 0 32768 i
r> 172.16.24.0/24 172.16.24.2 0 0 100 ?
*> 192.168.1.0 0.0.0.0 0 32768 i
R4#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.4.1.0/24 is directly connected, Loopback1
L 10.4.1.1/32 is directly connected, Loopback1
C 10.4.2.0/24 is directly connected, Loopback2
L 10.4.2.1/32 is directly connected, Loopback2
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.24.0/24 is directly connected, FastEthernet0/0
L 172.16.24.4/32 is directly connected, FastEthernet0/0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Loopback192
L 192.168.1.1/32 is directly connected, Loopback192
R6#sh ip bgp sum
BGP router identifier 172.16.26.6, local AS number 666
BGP table version is 33, main routing table version 33
4 network entries using 512 bytes of memory
4 path entries using 208 bytes of memory
2/2 BGP path/bestpath attribute entries using 248 bytes of memory
1 BGP AS-PATH entries using 24 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 992 total bytes of memory
BGP activity 13/9 prefixes, 18/14 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
172.16.26.2 4 100 14 14 33 0 0 00:09:03 1
R6#sh ip bgp
BGP table version is 33, local router ID is 172.16.26.6
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.6.1.0/24 0.0.0.0 0 32768 i
*> 10.6.2.0/24 0.0.0.0 0 32768 i
r> 172.16.26.0/24 172.16.26.2 0 0 100 ?
*> 192.168.1.0 0.0.0.0 0 32768 i
R6#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.6.1.0/24 is directly connected, Loopback1
L 10.6.1.1/32 is directly connected, Loopback1
C 10.6.2.0/24 is directly connected, Loopback2
L 10.6.2.1/32 is directly connected, Loopback2
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.26.0/24 is directly connected, FastEthernet0/0
L 172.16.26.6/32 is directly connected, FastEthernet0/0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Loopback192
L 192.168.1.1/32 is directly connected, Loopback192
If we see the configuration on R2 ASN 444 prefixes are exported with route-target value 444:4. This is extended community attached to all prefixes exported into BGP table from VRF BBB.
We can verify the same with show output on R2 for any route of VRF BBB.
R2#sh bgp vpnv4 unicast vrf BBB 10.4.2.0
BGP routing table entry for 444:4:10.4.2.0/24, version 3
Paths: (1 available, best #1, table BBB)
Advertised to update-groups:
7
444
172.16.24.4 from 172.16.24.4 (172.16.24.4)
Origin IGP, metric 0, localpref 100, valid, external, best
Extended Community: RT:444:4
mpls labels in/out 34/nolabel
Let’s import prefix from ASN 444 into VRF AAA on router R1.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#vrf definition AAA
R1(config-vrf)#address-family ipv4
R1(config-vrf-af)#route-target import ?
ASN:nn or IP-address:nn Target VPN Extended Community
R1(config-vrf-af)#route-target import 444:4
R1(config-vrf-af)#end
R1#
We can see the prefixes with extended community value 444:4 are imported into VRF AAA now. And the same would be advertised to BGP Peer R3.
R1#sh bgp vpnv4 unicast all
BGP table version is 16, local router ID is 172.16.0.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 333:3 (default for vrf AAA)
*> 10.3.1.0/24 172.16.13.3 0 0 333 i
*> 10.3.2.0/24 172.16.13.3 0 0 333 i
*>i10.4.1.0/24 172.16.0.2 0 100 0 444 i
*>i10.4.2.0/24 172.16.0.2 0 100 0 444 i
*> 172.16.13.0/24 0.0.0.0 0 32768 ?
*>i172.16.24.0/24 172.16.0.2 0 100 0 ?
*>i192.168.1.0 172.16.0.2 0 100 0 444 i
Route Distinguisher: 444:4
*>i10.4.1.0/24 172.16.0.2 0 100 0 444 i
*>i10.4.2.0/24 172.16.0.2 0 100 0 444 i
*>i172.16.24.0/24 172.16.0.2 0 100 0 ?
*>i192.168.1.0 172.16.0.2 0 100 0 444 i
Route Distinguisher: 666:6
*>i10.6.1.0/24 172.16.0.2 0 100 0 666 i
Network Next Hop Metric LocPrf Weight Path
*>i10.6.2.0/24 172.16.0.2 0 100 0 666 i
*>i172.16.26.0/24 172.16.0.2 0 100 0 ?
*>i192.168.1.0 172.16.0.2 0 100 0 666 i
BGP Table and Route table on R3:
R3#sh ip bgp sum
BGP router identifier 172.16.13.3, local AS number 333
BGP table version is 33, main routing table version 33
7 network entries using 896 bytes of memory
7 path entries using 364 bytes of memory
4/4 BGP path/bestpath attribute entries using 496 bytes of memory
2 BGP AS-PATH entries using 48 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 1804 total bytes of memory
BGP activity 18/11 prefixes, 19/12 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
172.16.13.1 4 100 44 44 33 0 0 00:35:47 5
R3#sh ip bgp
BGP table version is 33, local router ID is 172.16.13.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.3.1.0/24 0.0.0.0 0 32768 i
*> 10.3.2.0/24 0.0.0.0 0 32768 i
*> 10.4.1.0/24 172.16.13.1 0 100 444 i
*> 10.4.2.0/24 172.16.13.1 0 100 444 i
r> 172.16.13.0/24 172.16.13.1 0 0 100 ?
*> 172.16.24.0/24 172.16.13.1 0 100 ?
*> 192.168.1.0 172.16.13.1 0 100 444 i
R3#sh ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
B 10.4.1.0/24 [20/0] via 172.16.13.1, 00:02:43
B 10.4.2.0/24 [20/0] via 172.16.13.1, 00:02:43
172.16.0.0/16 is variably subnetted, 3 subnets, 2 masks
B 172.16.24.0/24 [20/0] via 172.16.13.1, 00:02:43
B 192.168.1.0/24 [20/0] via 172.16.13.1, 00:02:43
But we are receiving more prefix (all prefix advertised by R4) than our requirement.
We can use route-map with import-map under VRF to filter prefix as per our requirement.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip prefix-list R4-SELECTIVE-PREFIX seq 5 permit 10.4.2.0/24
R1(config)#
R1(config)#route-map AAA-VRF-IMPORT permit 10
R1(config-route-map)#match ip address prefix-list R4-SELECTIVE-PREFIX
R1(config-route-map)#exit
R1(config)#
R1(config)#vrf definition AAA
R1(config-vrf)#address-family ipv4
R1(config-vrf-af)#import map AAA-VRF-IMPORT
R1(config-vrf-af)#end
R1#
R1#clear bgp vpnv4 unicast * soft
Let’s do the same for import prefix from VRF CCC.
R1#
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip prefix-list R6-SELECTIVE-PREFIX seq 5 permit 10.6.1.0/24
R1(config)#
R1(config)#route-map AAA-VRF-IMPORT permit 20
R1(config-route-map)#match ip address prefix-list R6-SELECTIVE-PREFIX
R1(config-route-map)#
R1(config-route-map)#vrf definition AAA
R1(config-vrf)#address-family ipv4
R1(config-vrf-af)#route-target import 666:6
R1(config-vrf-af)#end
R1#
R1#clear bgp vpnv4 unicast * soft
R1#
Verify BGP table for VRF AAA on R1. Now it has imported only specific routes which are permitted by route-map.
R1#sh bgp vpnv4 unicast vrf AAA
BGP table version is 20, local router ID is 172.16.0.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 333:3 (default for vrf AAA)
*> 10.3.1.0/24 172.16.13.3 0 0 333 i
*> 10.3.2.0/24 172.16.13.3 0 0 333 i
*>i10.4.2.0/24 172.16.0.2 0 100 0 444 i
*>i10.6.1.0/24 172.16.0.2 0 100 0 666 i
*> 172.16.13.0/24 0.0.0.0 0 32768 ?
Verify BGP table and Routing table on R3:
R3#sh ip bgp
BGP table version is 37, local router ID is 172.16.13.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.3.1.0/24 0.0.0.0 0 32768 i
*> 10.3.2.0/24 0.0.0.0 0 32768 i
*> 10.4.2.0/24 172.16.13.1 0 100 444 i
*> 10.6.1.0/24 172.16.13.1 0 100 666 i
r> 172.16.13.0/24 172.16.13.1 0 0 100 ?
R3#sh ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
B 10.4.2.0/24 [20/0] via 172.16.13.1, 00:17:51
B 10.6.1.0/24 [20/0] via 172.16.13.1, 00:02:51
We have the route to reach remote networks of R4 and R6. Can we ping them?
R3#ping 10.4.2.1 source 10.3.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.2.1, timeout is 2 seconds:
Packet sent with a source address of 10.3.1.1
.....
Success rate is 0 percent (0/5)
No, WHY?
Because R4 and R6 don’t have route for R3’s networks to sent traffic back to R3.
R4#sh ip route 10.3.1.0
% Subnet not in table
We have to import VRF AAA’s routes into VRF BBB and CCC to get end-to-end reachability for these networks.
Apply below configuration on R2:
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#vrf definition BBB
R2(config-vrf)#address-family ipv4
R2(config-vrf-af)#route-target import 333:3
R2(config-vrf-af)#
R2(config-vrf-af)#vrf definition CCC
R2(config-vrf)#address-family ipv4
R2(config-vrf-af)#route-target import 333:3
R2(config-vrf-af)#end
R2#
R2#clear bgp vpnv4 unicast * soft
R2#
R2#
R2 is showing prefixes of VRF AAA imported into vrf BBB and CCC.
R2#sh bgp vpnv4 unicast all
BGP table version is 18, local router ID is 172.16.0.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 333:3
*>i10.3.1.0/24 172.16.0.1 0 100 0 333 i
*>i10.3.2.0/24 172.16.0.1 0 100 0 333 i
*>i172.16.13.0/24 172.16.0.1 0 100 0 ?
Route Distinguisher: 444:4 (default for vrf BBB)
*>i10.3.1.0/24 172.16.0.1 0 100 0 333 i
*>i10.3.2.0/24 172.16.0.1 0 100 0 333 i
*> 10.4.1.0/24 172.16.24.4 0 0 444 i
*> 10.4.2.0/24 172.16.24.4 0 0 444 i
*>i172.16.13.0/24 172.16.0.1 0 100 0 ?
*> 172.16.24.0/24 0.0.0.0 0 32768 ?
*> 192.168.1.0 172.16.24.4 0 0 444 i
Route Distinguisher: 666:6 (default for vrf CCC)
*>i10.3.1.0/24 172.16.0.1 0 100 0 333 i
*>i10.3.2.0/24 172.16.0.1 0 100 0 333 i
Network Next Hop Metric LocPrf Weight Path
*> 10.6.1.0/24 172.16.26.6 0 0 666 i
*> 10.6.2.0/24 172.16.26.6 0 0 666 i
*>i172.16.13.0/24 172.16.0.1 0 100 0 ?
*> 172.16.26.0/24 0.0.0.0 0 32768 ?
*> 192.168.1.0 172.16.26.6 0 0 666 i
R2#
Let’s verify BGP table and Route table of R4 and R6.
R4#sh ip bgp
BGP table version is 34, local router ID is 172.16.24.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.3.1.0/24 172.16.24.2 0 100 333 i
*> 10.3.2.0/24 172.16.24.2 0 100 333 i
*> 10.4.1.0/24 0.0.0.0 0 32768 i
*> 10.4.2.0/24 0.0.0.0 0 32768 i
*> 172.16.13.0/24 172.16.24.2 0 100 ?
r> 172.16.24.0/24 172.16.24.2 0 0 100 ?
*> 192.168.1.0 0.0.0.0 0 32768 i
R4#sh ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
B 10.3.1.0/24 [20/0] via 172.16.24.2, 00:01:59
B 10.3.2.0/24 [20/0] via 172.16.24.2, 00:01:59
172.16.0.0/16 is variably subnetted, 3 subnets, 2 masks
B 172.16.13.0/24 [20/0] via 172.16.24.2, 00:01:59
R4#sh ip route 10.3.1.0
Routing entry for 10.3.1.0/24
Known via "bgp 444", distance 20, metric 0
Tag 100, type external
Last update from 172.16.24.2 00:02:05 ago
Routing Descriptor Blocks:
* 172.16.24.2, from 172.16.24.2, 00:02:05 ago
Route metric is 0, traffic share count is 1
AS Hops 2
Route tag 100
MPLS label: none
R4#
R6#sh ip bgp
BGP table version is 36, local router ID is 172.16.26.6
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.3.1.0/24 172.16.26.2 0 100 333 i
*> 10.3.2.0/24 172.16.26.2 0 100 333 i
*> 10.6.1.0/24 0.0.0.0 0 32768 i
*> 10.6.2.0/24 0.0.0.0 0 32768 i
*> 172.16.13.0/24 172.16.26.2 0 100 ?
r> 172.16.26.0/24 172.16.26.2 0 0 100 ?
*> 192.168.1.0 0.0.0.0 0 32768 i
R6#
R6#sh ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
B 10.3.1.0/24 [20/0] via 172.16.26.2, 00:02:29
B 10.3.2.0/24 [20/0] via 172.16.26.2, 00:02:29
172.16.0.0/16 is variably subnetted, 3 subnets, 2 masks
B 172.16.13.0/24 [20/0] via 172.16.26.2, 00:02:29
R6#
Now check end-to-end connectivity with Ping from R3 to R4 and R6 networks.
R3#ping 10.4.2.1 source 10.3.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.2.1, timeout is 2 seconds:
Packet sent with a source address of 10.3.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/51/76 ms
R3#ping 10.6.1.1 source 10.3.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.6.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.3.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 44/52/64 ms
Everything looks fine so far.
We got another requirement. On Router R1, VRF AAA has to import prefix 192.168.1.0/24 from VRF BBB.
Currently we are using below prefix-list and route-map:
R1#sh run | s prefix-list|route-map
ip prefix-list R4-SELECTIVE-PREFIX seq 5 permit 10.4.2.0/24
ip prefix-list R6-SELECTIVE-PREFIX seq 5 permit 10.6.1.0/24
route-map AAA-VRF-IMPORT permit 10
match ip address prefix-list R4-SELECTIVE-PREFIX
route-map AAA-VRF-IMPORT permit 20
match ip address prefix-list R6-SELECTIVE-PREFIX
If we create another prefix list entry to permit 192.168.1.0/24, We should be all set.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip prefix-list R4-SELECTIVE-PREFIX seq 10 permit 192.168.1.0/24
R1(config)#end
R1#
Let’s verify routing table on R3. We have route for 192.168.1.0/24 now.
R3#sh ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
B 10.4.2.0/24 [20/0] via 172.16.13.1, 00:41:07
B 10.6.1.0/24 [20/0] via 172.16.13.1, 00:26:07
B 192.168.1.0/24 [20/0] via 172.16.13.1, 00:00:06
And we can ping remote network also.
R3#ping 192.168.1.1 source 10.3.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.3.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/39/56 ms
Everything looks fine.
Let’s goto Router R4 and shutdown interface Loopback 192 which is used for network 192.168.1.0/24
R4#sh run int l192
Building configuration...
Current configuration : 67 bytes
!
interface Loopback192
ip address 192.168.1.1 255.255.255.0
end
R4#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R4(config)#int l192
R4(config-if)#shut
R4(config-if)#
R4(config-if)#
*Jun 4 19:29:03.474: %LINK-5-CHANGED: Interface Loopback192, changed state to administratively down
*Jun 4 19:29:04.474: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback192, changed state to down
R4(config-if)#
Now goto Router R3 and try to ping 192.168.1.1 again. It should not be working, right?
But it can still ping it 
Let’s see who is this 192.168.1.1 device.
R3#192.168.1.1
Trying 192.168.1.1 ... Open
User Access Verification
Password:
R6#
Hmm..we are receiving 192.168.1.0/24 prefix from R6(VRF CCC).
Let’s enable interface loopback192 on R4.
R4(config-if)#no shut
R4(config-if)#end
R4#
*Jun 4 19:31:05.626: %LINK-3-UPDOWN: Interface Loopback192, changed state to up
*Jun 4 19:31:06.490: %SYS-5-CONFIG_I: Configured from console by console
R4#
*Jun 4 19:31:06.626: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback192, changed state to up
R4#
Let’s see what is happening on Router R1 for importing routes from other VRFs.
R1#sh bgp vpnv4 unicast all
BGP table version is 24, local router ID is 172.16.0.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 333:3 (default for vrf AAA)
*> 10.3.1.0/24 172.16.13.3 0 0 333 i
*> 10.3.2.0/24 172.16.13.3 0 0 333 i
*>i10.4.2.0/24 172.16.0.2 0 100 0 444 i
*>i10.6.1.0/24 172.16.0.2 0 100 0 666 i
*> 172.16.13.0/24 0.0.0.0 0 32768 ?
* i192.168.1.0 172.16.0.2 0 100 0 444 i
*>i 172.16.0.2 0 100 0 666 i
Route Distinguisher: 444:4
*>i10.4.1.0/24 172.16.0.2 0 100 0 444 i
*>i10.4.2.0/24 172.16.0.2 0 100 0 444 i
*>i172.16.24.0/24 172.16.0.2 0 100 0 ?
*>i192.168.1.0 172.16.0.2 0 100 0 444 i
Route Distinguisher: 666:6
*>i10.6.1.0/24 172.16.0.2 0 100 0 666 i
Network Next Hop Metric LocPrf Weight Path
*>i10.6.2.0/24 172.16.0.2 0 100 0 666 i
*>i172.16.26.0/24 172.16.0.2 0 100 0 ?
*>i192.168.1.0 172.16.0.2 0 100 0 666 i
R1#
It has imported this route from two different VRFs (BBB and CCC)
R1#sh bgp vpnv4 unicast vrf AAA 192.168.1.0
BGP routing table entry for 333:3:192.168.1.0/24, version 23
Paths: (2 available, best #2, table AAA)
Advertised to update-groups:
5
444, imported path from 444:4:192.168.1.0/24
172.16.0.2 (metric 2) from 172.16.0.2 (172.16.0.2)
Origin IGP, metric 0, localpref 100, valid, internal
Extended Community: RT:444:4
mpls labels in/out nolabel/21
666, imported path from 666:6:192.168.1.0/24
172.16.0.2 (metric 2) from 172.16.0.2 (172.16.0.2)
Origin IGP, metric 0, localpref 100, valid, internal, best
Extended Community: RT:666:6
mpls labels in/out nolabel/38
This is not our requirement. We want to import it only from VRF BBB.
We have to match prefix along with extended community value to achieve this goal.
Create extended-community list and match it inside route-map.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip extcommunity-list standard FROM-R4 permit rt 444:4
R1(config)#ip extcommunity-list standard FROM-R6 permit rt 666:6
R1(config)#
R1(config)#route-map AAA-VRF-IMPORT permit 10
R1(config-route-map)#match extcommunity FROM-R4
R1(config-route-map)#route-map AAA-VRF-IMPORT permit 20
R1(config-route-map)#match extcommunity FROM-R6
R1(config-route-map)#end
R1#
We have this configuration now:
R1#sh run | s prefix|extcommunity-list|route-map
ip extcommunity-list standard FROM-R4 permit rt 444:4
ip extcommunity-list standard FROM-R6 permit rt 666:6
ip prefix-list R4-SELECTIVE-PREFIX seq 5 permit 10.4.2.0/24
ip prefix-list R4-SELECTIVE-PREFIX seq 10 permit 192.168.1.0/24
ip prefix-list R6-SELECTIVE-PREFIX seq 5 permit 10.6.1.0/24
route-map AAA-VRF-IMPORT permit 10
match ip address prefix-list R4-SELECTIVE-PREFIX
match extcommunity FROM-R4
route-map AAA-VRF-IMPORT permit 20
match ip address prefix-list R6-SELECTIVE-PREFIX
match extcommunity FROM-R6
R1#
Here route-map would use Boolean AND logic and permit prefix if it is matched by BOTH conditions, prefix-list and extended-community value.
Route-map sequence #10 will match prefixes 10.4.2.0/24 and 192.168.1.0/24 if they have RT extended-community value 444:4 only.
Similarily Route-map sequence #20 will match prefixes 10.6.1.0/24 if it has RT extended-community value 666:6 only.
Verify VRF AAA BGP table now on Router R1.
R1#sh bgp vpnv4 unicast vrf AAA
BGP table version is 25, local router ID is 172.16.0.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 333:3 (default for vrf AAA)
*> 10.3.1.0/24 172.16.13.3 0 0 333 i
*> 10.3.2.0/24 172.16.13.3 0 0 333 i
*>i10.4.2.0/24 172.16.0.2 0 100 0 444 i
*>i10.6.1.0/24 172.16.0.2 0 100 0 666 i
*> 172.16.13.0/24 0.0.0.0 0 32768 ?
*>i192.168.1.0 172.16.0.2 0 100 0 444 i
R1#sh bgp vpnv4 unicast vrf AAA 192.168.1.0
BGP routing table entry for 333:3:192.168.1.0/24, version 25
Paths: (1 available, best #1, table AAA)
Advertised to update-groups:
5
444, imported path from 444:4:192.168.1.0/24
172.16.0.2 (metric 2) from 172.16.0.2 (172.16.0.2)
Origin IGP, metric 0, localpref 100, valid, internal, best
Extended Community: RT:444:4
mpls labels in/out nolabel/21
Verify BGP table, reachability from R3 for all remote networks.
R3#sh ip bgp
BGP table version is 40, local router ID is 172.16.13.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.3.1.0/24 0.0.0.0 0 32768 i
*> 10.3.2.0/24 0.0.0.0 0 32768 i
*> 10.4.2.0/24 172.16.13.1 0 100 444 i
*> 10.6.1.0/24 172.16.13.1 0 100 666 i
r> 172.16.13.0/24 172.16.13.1 0 0 100 ?
*> 192.168.1.0 172.16.13.1 0 100 444 i
R3#sh ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
B 10.4.2.0/24 [20/0] via 172.16.13.1, 01:02:20
B 10.6.1.0/24 [20/0] via 172.16.13.1, 00:47:20
B 192.168.1.0/24 [20/0] via 172.16.13.1, 00:08:19
R3#ping 10.4.2.1 source 10.3.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.2.1, timeout is 2 seconds:
Packet sent with a source address of 10.3.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/48/60 ms
R3#ping 10.6.1.1 source 10.3.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.6.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.3.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/49/64 ms
R3#ping 192.168.1.1 source 10.3.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.3.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 24/45/72 ms
Final Configuration on R1 and R2.
R1:
vrf definition AAA
rd 333:3
!
address-family ipv4
import map AAA-VRF-IMPORT
route-target export 333:3
route-target import 333:3
route-target import 444:4
route-target import 666:6
exit-address-family
!
interface Loopback0
ip address 172.16.0.1 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 172.16.12.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface FastEthernet1/0
vrf forwarding AAA
ip address 172.16.13.1 255.255.255.0
speed 100
duplex full
!
router ospf 1
log-adjacency-changes
!
router bgp 100
bgp router-id 172.16.0.1
no bgp default ipv4-unicast
no bgp default route-target filter
bgp log-neighbor-changes
neighbor 172.16.0.2 remote-as 100
neighbor 172.16.0.2 update-source Loopback0
!
address-family ipv4
no synchronization
no auto-summary
exit-address-family
!
address-family vpnv4
neighbor 172.16.0.2 activate
neighbor 172.16.0.2 send-community extended
exit-address-family
!
address-family ipv4 vrf AAA
no synchronization
redistribute connected
neighbor 172.16.13.3 remote-as 333
neighbor 172.16.13.3 activate
exit-address-family
!
!
ip extcommunity-list standard FROM-R4 permit rt 444:4
ip extcommunity-list standard FROM-R6 permit rt 666:6
!
ip prefix-list R4-SELECTIVE-PREFIX seq 5 permit 10.4.2.0/24
ip prefix-list R4-SELECTIVE-PREFIX seq 10 permit 192.168.1.0/24
!
ip prefix-list R6-SELECTIVE-PREFIX seq 5 permit 10.6.1.0/24
!
route-map AAA-VRF-IMPORT permit 10
match ip address prefix-list R4-SELECTIVE-PREFIX
match extcommunity FROM-R4
!
route-map AAA-VRF-IMPORT permit 20
match ip address prefix-list R6-SELECTIVE-PREFIX
match extcommunity FROM-R6
!
R2:
vrf definition BBB
rd 444:4
!
address-family ipv4
route-target export 444:4
route-target import 444:4
route-target import 333:3
exit-address-family
!
vrf definition CCC
rd 666:6
!
address-family ipv4
route-target export 666:6
route-target import 666:6
route-target import 333:3
exit-address-family
!
interface Loopback0
ip address 172.16.0.2 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 172.16.12.2 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface FastEthernet1/0
vrf forwarding BBB
ip address 172.16.24.2 255.255.255.0
!
interface FastEthernet1/1
vrf forwarding CCC
ip address 172.16.26.2 255.255.255.0
!
router ospf 1
log-adjacency-changes
!
router bgp 100
bgp router-id 172.16.0.2
no bgp default ipv4-unicast
no bgp default route-target filter
bgp log-neighbor-changes
neighbor 172.16.0.1 remote-as 100
neighbor 172.16.0.1 update-source Loopback0
!
address-family ipv4
no synchronization
no auto-summary
exit-address-family
!
address-family vpnv4
neighbor 172.16.0.1 activate
neighbor 172.16.0.1 send-community extended
exit-address-family
!
address-family ipv4 vrf BBB
no synchronization
redistribute connected
neighbor 172.16.24.4 remote-as 444
neighbor 172.16.24.4 activate
exit-address-family
!
address-family ipv4 vrf CCC
no synchronization
redistribute connected
neighbor 172.16.26.6 remote-as 666
neighbor 172.16.26.6 activate
exit-address-family