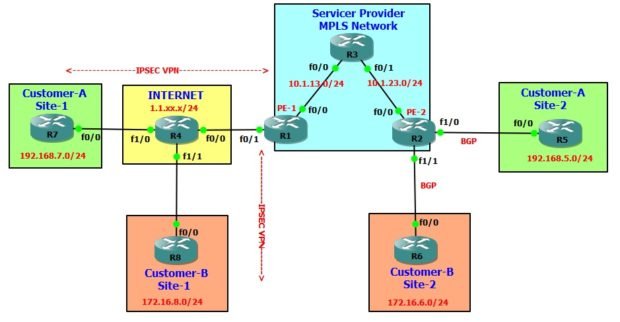
In part 2, We will discuss the VRF Aware IPSec VPN when internet link is not configured under Global VRF and it belongs to a specific VRF which would be FVRF (Front Door VRF) in this scenario.
You must refer part 1 http://www.amolak.net/vrf-aware-ipsec-vpn-part-1/ of this discussion to understand the terminologies used. Also we will use the same network topology of part1.
Configuration:
R1 - PE and VRF Aware IPSec VPN Router !! -- Create VRF named cust-a for Customer-A --!! !! -- This is Inside VRF (I-VRF) --!! vrf definition cust-a rd 123:1 ! address-family ipv4 route-target export 123:1 route-target import 123:1 exit-address-family ! !! -- Create VRF named cust-b for Customer-B --!! !! -- This is Inside VRF (I-VRF) --!! ! vrf definition cust-b rd 123:2 ! address-family ipv4 route-target export 123:2 route-target import 123:2 exit-address-family ! !! -- Create VRF named int-vrf for Internet Link --!! !! -- This is Front Door VRF (F-VRF) --!! ! vrf definition int-vrf rd 123:123 ! address-family ipv4 route-target export 123:123 route-target import 123:123 exit-address-family ! interface FastEthernet0/1 vrf forwarding int-vrf ip address 1.1.14.1 255.255.255.0 ! !! -- Define ISAKMP Pre-shared key for both VPN Peers --!! ! crypto keyring internet-keyring vrf int-vrf pre-shared-key address 1.1.47.7 key vpn1password pre-shared-key address 1.1.48.8 key vpn2password ! !! -- Create ISAKMP Policy --!! ! crypto isakmp policy 1 encr 3des authentication pre-share group 2 ! !! -- Create ISAKMP Profile for both VPNs --!! ! crypto isakmp profile vpn1 vrf cust-a keyring internet-keyring match identity address 1.1.47.7 255.255.255.255 int-vrf crypto isakmp profile vpn2 vrf cust-b keyring internet-keyring match identity address 1.1.48.8 255.255.255.255 int-vrf ! ! !! -- Create IPSec Transform-set for both VPNs --!! ! crypto ipsec transform-set vpn1-TS esp-3des esp-sha-hmac mode tunnel crypto ipsec transform-set vpn2-TS esp-3des esp-sha-hmac mode tunnel ! ! !! -- Create access-list to define the traffic to pass through --!! !! -- the VPN tunnel --!! !! -- access-list 101 is for Customer-1 traffic --!! !! -- access-list 102 is for Customer-2 traffic --!! ! access-list 101 permit ip 192.168.5.0 0.0.0.255 192.168.7.0 0.0.0.255 access-list 102 permit ip 172.16.6.0 0.0.0.255 172.16.8.0 0.0.0.255 ! !! -- Create Crypto MAP for both VPNs --!! ! crypto map crypmap 1 ipsec-isakmp set peer 1.1.47.7 set transform-set vpn1-TS set isakmp-profile vpn1 match address 101 ! crypto map crypmap 2 ipsec-isakmp set peer 1.1.48.8 set transform-set vpn2-TS set isakmp-profile vpn2 match address 102 ! !! -- Apply Crypto MAP to Internet facing interface --!! ! interface FastEthernet0/1 vrf forwarding int-vrf ip address 1.1.14.1 255.255.255.0 crypto map crypmap ! !! -- Routing --!! !! -- We have to import default route from VRF 'int-vrf' --!! !! -- into Customer VRFs 'cust-a' and 'cust-b'--!! !! -- Without this route import, both customer VRF has --!! !! -- no idea how to reach internet and VPN peers --!! ! vrf definition cust-a address-family ipv4 route-target import 123:123 exit-address-family ! vrf definition cust-b address-family ipv4 route-target import 123:123 exit-address-family ! !! -- Static route - VRF 'int-vrf' --!! ip route vrf int-vrf 0.0.0.0 0.0.0.0 1.1.14.4 !! -- Static route - VRF 'cust-a' --!! ip route vrf cust-a 192.168.7.0 255.255.255.0 FastEthernet0/1 1.1.14.4 !! -- Static route - VRF 'cust-b' --!! ip route vrf cust-b 172.16.8.0 255.255.255.0 FastEthernet0/1 1.1.14.4 ! ! !! -- Redistribute IPSec VPN routes into BGP --!! !! -- MP-BGP will advertise it to PE-2 Router --!! !! -- PE-2 Router will advertise those routes to Customers --!! ! router bgp 123 bgp router-id 10.1.0.1 bgp log-neighbor-changes no bgp default ipv4-unicast neighbor 10.1.0.2 remote-as 123 neighbor 10.1.0.2 update-source Loopback0 ! address-family ipv4 exit-address-family ! address-family vpnv4 neighbor 10.1.0.2 activate neighbor 10.1.0.2 send-community extended exit-address-family ! address-family ipv4 vrf cust-a redistribute static exit-address-family ! address-family ipv4 vrf cust-b redistribute static exit-address-family !
Verification: R7 (Customer-A Site 1) can ping R5 (Customer-A Site-2) network R7#ping 192.168.5.5 so 192.168.7.7 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.5.5, timeout is 2 seconds: Packet sent with a source address of 192.168.7.7 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 124/129/140 ms R8 (Customer-B Site 1) can ping R6 (Customer-B Site-2) network R8#ping 172.16.6.6 so 172.16.8.8 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.6.6, timeout is 2 seconds: Packet sent with a source address of 172.16.8.8 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 108/132/144 ms Verify VPN Status on R1 R1#show crypto session detail Crypto session current status Code: C - IKE Configuration mode, D - Dead Peer Detection K - Keepalives, N - NAT-traversal, T - cTCP encapsulation X - IKE Extended Authentication, F - IKE Fragmentation Interface: FastEthernet0/1 Profile: vpn1 Uptime: 00:25:30 Session status: UP-ACTIVE Peer: 1.1.47.7 port 500 fvrf: int-vrf ivrf: cust-a Phase1_id: 1.1.47.7 Desc: (none) IKEv1 SA: local 1.1.14.1/500 remote 1.1.47.7/500 Active Capabilities:(none) connid:1001 lifetime:23:34:29 IPSEC FLOW: permit ip 192.168.5.0/255.255.255.0 192.168.7.0/255.255.255.0 Active SAs: 2, origin: crypto map Inbound: #pkts dec'ed 34 drop 0 life (KB/Sec) 4171386/2069 Outbound: #pkts enc'ed 34 drop 0 life (KB/Sec) 4171386/2069 Interface: FastEthernet0/1 Profile: vpn2 Uptime: 00:25:07 Session status: UP-ACTIVE Peer: 1.1.48.8 port 500 fvrf: int-vrf ivrf: cust-b Phase1_id: 1.1.48.8 Desc: (none) IKEv1 SA: local 1.1.14.1/500 remote 1.1.48.8/500 Active Capabilities:(none) connid:1002 lifetime:23:34:52 IPSEC FLOW: permit ip 172.16.6.0/255.255.255.0 172.16.8.0/255.255.255.0 Active SAs: 2, origin: crypto map Inbound: #pkts dec'ed 14 drop 0 life (KB/Sec) 4267407/2092 Outbound: #pkts enc'ed 14 drop 0 life (KB/Sec) 4267407/2092 Here, we can see Front Door VRF (FVRF) is 'int-vrf' and Inside VRF (IVRF) is 'cust-a' & 'cust-b' for Customer A and B respectively.
Here is the Full configuration of Router R1. There is no change in the configuration of all other devices. It is same as mentioned in part-1.
hostname R1
!
vrf definition cust-a
rd 123:1
!
address-family ipv4
route-target export 123:1
route-target import 123:1
route-target import 123:123
exit-address-family
!
vrf definition cust-b
rd 123:2
!
address-family ipv4
route-target export 123:2
route-target import 123:2
route-target import 123:123
exit-address-family
!
vrf definition int-vrf
rd 123:123
!
address-family ipv4
route-target export 123:123
route-target import 123:123
exit-address-family
!
crypto keyring internet-keyring vrf int-vrf
pre-shared-key address 1.1.47.7 key vpn1password
pre-shared-key address 1.1.48.8 key vpn2password
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp profile vpn1
vrf cust-a
keyring internet-keyring
match identity address 1.1.47.7 255.255.255.255 int-vrf
crypto isakmp profile vpn2
vrf cust-b
keyring internet-keyring
match identity address 1.1.48.8 255.255.255.255 int-vrf
!
!
crypto ipsec transform-set vpn1-TS esp-3des esp-sha-hmac
mode tunnel
crypto ipsec transform-set vpn2-TS esp-3des esp-sha-hmac
mode tunnel
!
!
!
crypto map crypmap 1 ipsec-isakmp
set peer 1.1.47.7
set transform-set vpn1-TS
set isakmp-profile vpn1
match address 101
crypto map crypmap 2 ipsec-isakmp
set peer 1.1.48.8
set transform-set vpn2-TS
set isakmp-profile vpn2
match address 102
!
interface Loopback0
ip address 10.1.0.1 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 10.1.13.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
speed 100
duplex full
mpls ip
!
interface FastEthernet0/1
vrf forwarding int-vrf
ip address 1.1.14.1 255.255.255.0
speed 100
duplex full
crypto map crypmap
!
router ospf 1
router-id 10.1.0.1
!
router bgp 123
bgp router-id 10.1.0.1
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 10.1.0.2 remote-as 123
neighbor 10.1.0.2 update-source Loopback0
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 10.1.0.2 activate
neighbor 10.1.0.2 send-community extended
exit-address-family
!
address-family ipv4 vrf cust-a
redistribute static
exit-address-family
!
address-family ipv4 vrf cust-b
redistribute static
exit-address-family
!
address-family ipv4 vrf int-vrf
redistribute connected
redistribute static
exit-address-family
!
ip route vrf cust-a 192.168.7.0 255.255.255.0 FastEthernet0/1 1.1.14.4
ip route vrf cust-b 172.16.8.0 255.255.255.0 FastEthernet0/1 1.1.14.4
ip route vrf int-vrf 0.0.0.0 0.0.0.0 1.1.14.4
!
access-list 101 permit ip 192.168.5.0 0.0.0.255 192.168.7.0 0.0.0.255
access-list 102 permit ip 172.16.6.0 0.0.0.255 172.16.8.0 0.0.0.255
!
end